Google
Course Description
Build real-time, authenticated, scalable, and secure apps on Firebase. You’ll learn how to do real-time updates with Firestore. Create security rules and sign in users with Firebase Authentication – without needing to run a server! And you’ll even be able to trigger events that run server code using Cloud Functions.
This course and others like it are available as part of our Frontend Masters video subscription.
Preview
CloseWhat They're Saying
I just completed "Firebase Fundamentals" course by David East (Google) on Frontend Masters!
I've been using Firebase informally for almost 4 years but now I've just discovered tons of great tips and best practices in the course. Big thanks David

Amani Bisimwa
AmaniBisimwa4
I just completed "Firebase Fundamentals" by David East (Google) on Frontend Masters!
What an amazing class, I recommend the course to everyone who wants to start with Firebase! Well explained, hats off David 😊

Shekinah Tshiokufila
tshiokufila
Table of Contents
Introduction
Section Duration: 8 minutes
 David East introduces the course by walking through the required installations and where to find the course materials. An overview of Firebase, including the architecture, libraries, and general workflow, is also covered in this segment.
David East introduces the course by walking through the required installations and where to find the course materials. An overview of Firebase, including the architecture, libraries, and general workflow, is also covered in this segment.
Setup
Section Duration: 58 minutes
 David demonstrates how to quickly set up a Firebase project by configuring a Firebase App, which includes a JavaScript SDK and a Firebase CLI. A Student's question regarding if the initialize app config is different in an SSR library such as Next.js is also covered in this segment.
David demonstrates how to quickly set up a Firebase project by configuring a Firebase App, which includes a JavaScript SDK and a Firebase CLI. A Student's question regarding if the initialize app config is different in an SSR library such as Next.js is also covered in this segment. David walks through connecting to a Firestore database by pulling in markdown that has been converted into HTML and discusses how working with Firestore data compares to using SQL. Setting a document, deleting a document, and receiving the results in a callback are covered in this segment.
David walks through connecting to a Firestore database by pulling in markdown that has been converted into HTML and discusses how working with Firestore data compares to using SQL. Setting a document, deleting a document, and receiving the results in a callback are covered in this segment. David discusses implementing Firebase authentication using the Anonymous authentication provider, which can also provide guest authentication. Firebase Authentication is a fully managed authentication system for signing in and managing users without needing a designated server.
David discusses implementing Firebase authentication using the Anonymous authentication provider, which can also provide guest authentication. Firebase Authentication is a fully managed authentication system for signing in and managing users without needing a designated server. David demonstrates logging into and setting up the Firebase CLI to deploy web applications. A student's question regarding the difference between the doc and setDoc function is also covered in this segment.
David demonstrates logging into and setting up the Firebase CLI to deploy web applications. A student's question regarding the difference between the doc and setDoc function is also covered in this segment. David discusses what went against best practices in the previous Firebase demo and briefly demonstrates implementing best practices for security, code structure, production services, deployment, and data models. A student's question regarding if Firebase sets up a WebSocket when talking to the database is also covered in this segment.
David discusses what went against best practices in the previous Firebase demo and briefly demonstrates implementing best practices for security, code structure, production services, deployment, and data models. A student's question regarding if Firebase sets up a WebSocket when talking to the database is also covered in this segment.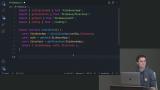 David walks through connecting to the Auth and Firestore emulators, the contents of the firebase.json file, and enabling the Emulator UI. Student questions regarding how often the offline data store updates and caches data and if users and data can be populated in a development environment are also covered in this segment.
David walks through connecting to the Auth and Firestore emulators, the contents of the firebase.json file, and enabling the Emulator UI. Student questions regarding how often the offline data store updates and caches data and if users and data can be populated in a development environment are also covered in this segment.
Firestore
Section Duration: 43 minutes
 David provides an overview of SQL databases, translates those concepts onto NoSQL databases, and provides pros and cons for both approaches. Firestore is a NoSQL document database with real-time and offline capabilities.
David provides an overview of SQL databases, translates those concepts onto NoSQL databases, and provides pros and cons for both approaches. Firestore is a NoSQL document database with real-time and offline capabilities. David demonstrates retrieving data from Firestore by attaching a collection or document reference to the onSnapshot method. Using mutation functions such as setDoc, updateDoc, and deleteDoc to write data, generating path Ids, and server timestamps are also covered in this segment.
David demonstrates retrieving data from Firestore by attaching a collection or document reference to the onSnapshot method. Using mutation functions such as setDoc, updateDoc, and deleteDoc to write data, generating path Ids, and server timestamps are also covered in this segment.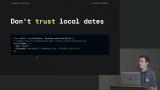 David discusses the difficulty of incrementing data on a real-time system, avoiding update errors by utilizing generated IDs, and an overview of the offline cache. Student questions regarding if there is a limit to the number of listeners on paths and how to indicate a disconnection from Firestore are also covered in this segment.
David discusses the difficulty of incrementing data on a real-time system, avoiding update errors by utilizing generated IDs, and an overview of the offline cache. Student questions regarding if there is a limit to the number of listeners on paths and how to indicate a disconnection from Firestore are also covered in this segment. Students are instructed to create realtime streams and map over the data.
Students are instructed to create realtime streams and map over the data.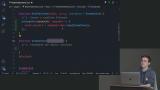 David walks through the solution to the Firestore realtime stream exercise.
David walks through the solution to the Firestore realtime stream exercise.
Querying
Section Duration: 1 hour, 4 minutes
 David briefly discusses simple and composite queries and walks through query operators, including equality, in, greater than, less than, and not-in. Simple queries involve querying based on one field, while composite queries involve querying based on more than one field.
David briefly discusses simple and composite queries and walks through query operators, including equality, in, greater than, less than, and not-in. Simple queries involve querying based on one field, while composite queries involve querying based on more than one field. David live codes examples of simple queries, including limited queries, queries for specific categories, less than queries, and queries for data within a set date range.
David live codes examples of simple queries, including limited queries, queries for specific categories, less than queries, and queries for data within a set date range.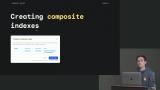 David discusses creating custom sorted composite indexes for quick database querying. Student questions regarding if there is support for or queries, if queries can be ordered by date, and if there is a way to get queries back in random order are also covered in this segment.
David discusses creating custom sorted composite indexes for quick database querying. Student questions regarding if there is support for or queries, if queries can be ordered by date, and if there is a way to get queries back in random order are also covered in this segment. Students are instructed to write a query for all expenses not categorized as fun, clothes, gifts, home, or personal, and a query for all expenses categorized as 'food' and occurred in January 2021 but not on 12/26/2021.
Students are instructed to write a query for all expenses not categorized as fun, clothes, gifts, home, or personal, and a query for all expenses categorized as 'food' and occurred in January 2021 but not on 12/26/2021. David walks through the solution to the composite queries exercise.
David walks through the solution to the composite queries exercise. David walks through querying through arrays with array operators such as array-contains and array-contains-any. A more complicated example of querying a date range with set excluded dates is also demonstrated in this segment.
David walks through querying through arrays with array operators such as array-contains and array-contains-any. A more complicated example of querying a date range with set excluded dates is also demonstrated in this segment.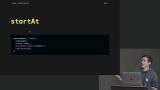 David demonstrates dividing large query results into smaller discrete pages using startAt and endAt to create references to data ranges.
David demonstrates dividing large query results into smaller discrete pages using startAt and endAt to create references to data ranges.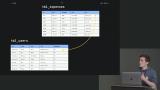 David discusses the difference between joins in SQL and NoSQL databases and the hierarchy of the document structure. How to update repeated data located in multiple collections and query across all subcollections is also covered in this segment.
David discusses the difference between joins in SQL and NoSQL databases and the hierarchy of the document structure. How to update repeated data located in multiple collections and query across all subcollections is also covered in this segment.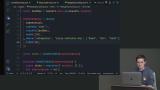 David demonstrates the flexibility of NoSQL databases by walking through a few examples of collection group queries.
David demonstrates the flexibility of NoSQL databases by walking through a few examples of collection group queries. David discusses handling when an operation fails by making the process atomic with batched writes and transactions. Transactions run multiple operations in an atomic process including the access to reading data.
David discusses handling when an operation fails by making the process atomic with batched writes and transactions. Transactions run multiple operations in an atomic process including the access to reading data.
Authorization & Security
Section Duration: 1 hour, 35 minutes
 David provides an overview of Firebase Auth, a serverless authentication provider with integration into Firebase security rules. A demo walkthrough of authenticating users, linking accounts, and admin permissions is also provided in this segment.
David provides an overview of Firebase Auth, a serverless authentication provider with integration into Firebase security rules. A demo walkthrough of authenticating users, linking accounts, and admin permissions is also provided in this segment. David answers student questions regarding what anonymous login looks like, if there are any specifications to follow to create a custom auth provider, and how to decide which kind of auth to use.
David answers student questions regarding what anonymous login looks like, if there are any specifications to follow to create a custom auth provider, and how to decide which kind of auth to use. David discusses Security Rules as being used to determine access to Firebase resources on every request and live codes some Security Rules. Security Rules are centralized, written in a custom language, and must match at the document level.
David discusses Security Rules as being used to determine access to Firebase resources on every request and live codes some Security Rules. Security Rules are centralized, written in a custom language, and must match at the document level. David walks through examples demonstrating testing and writing Security Rules to determine authenticated and unauthenticated users.
David walks through examples demonstrating testing and writing Security Rules to determine authenticated and unauthenticated users.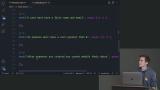 David live codes examples of structural Security Rules, which determine that the data sent to the server is the data the server expects. A demonstration of the Firestore request monitor is also provided in this segment.
David live codes examples of structural Security Rules, which determine that the data sent to the server is the data the server expects. A demonstration of the Firestore request monitor is also provided in this segment.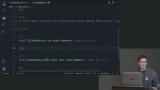 David walks through examples of role-based access control Security Rules to determine a user's role and what that role has access to.
David walks through examples of role-based access control Security Rules to determine a user's role and what that role has access to. David discusses functions that allow writing server code in response to events within Firebase without needing a server known as Cloud Functions. Functions are considered a trusted environment, allowing the Admin SDK to be used.
David discusses functions that allow writing server code in response to events within Firebase without needing a server known as Cloud Functions. Functions are considered a trusted environment, allowing the Admin SDK to be used.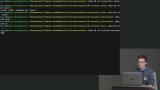 David walks through examples demonstrating using Cloud functions to set a CDN cache for an hour and make an HTTP request. This segment also covers configuring the firebase.json file to connect to Firebase hosting.
David walks through examples demonstrating using Cloud functions to set a CDN cache for an hour and make an HTTP request. This segment also covers configuring the firebase.json file to connect to Firebase hosting.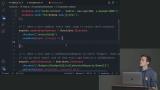 David live codes an example of a Cloud Function triggered by a document event. Users changing their data will trigger the Cloud Function to update it across all expenses.
David live codes an example of a Cloud Function triggered by a document event. Users changing their data will trigger the Cloud Function to update it across all expenses. David walks through an advanced use case for a Cloud Function to write a request to create a subcollection, look up a user by email with the Admin SDK, and add them as collaborators.
David walks through an advanced use case for a Cloud Function to write a request to create a subcollection, look up a user by email with the Admin SDK, and add them as collaborators. David walks through a continuation of the Admin SDK example by checking if a new user has any pre-existing collaborator requests and, if so, adding them as collaborators. A brief discussion regarding the auth triggers onCreate and onDelete and the v2 blocking functions beforeCreate and beforeSignIn.
David walks through a continuation of the Admin SDK example by checking if a new user has any pre-existing collaborator requests and, if so, adding them as collaborators. A brief discussion regarding the auth triggers onCreate and onDelete and the v2 blocking functions beforeCreate and beforeSignIn.
Wrapping Up
Section Duration: 2 minutes
 David wraps up the course by providing a brief overview of Firebase and answering a student's question regarding how to handle data that originates from an external system.
David wraps up the course by providing a brief overview of Firebase and answering a student's question regarding how to handle data that originates from an external system.
Learn Straight from the Experts Who Shape the Modern Web
- In-depth Courses
- Industry Leading Experts
- Learning Paths
- Live Interactive Workshops

