Temporal
Course Description
Take control of your application's security! Learn how to protect against common vulnerabilities every developer should know, such as session hijacking, SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). Gain hands-on experience with security tools and pick up best practices for writing more secure JavaScript in your web applications.
This course and others like it are available as part of our Frontend Masters video subscription.
Preview
Course Details
Published: August 20, 2024
Rating
Learning Paths
Topics
Learn Straight from the Experts Who Shape the Modern Web
Your Path to Senior Developer and Beyond
- 250+ In-depth courses
- 24 Learning Paths
- Industry Leading Experts
- Live Interactive Workshops
Table of Contents
Introduction
Section Duration: 15 minutes
 Steve Kinney introduces the course by discussing the challenges of web security, as well as the importance of understanding the mental model of security on the web. This course will cover common vulnerabilities found in web applications and explore ways to break them open to gain a deeper understanding of web security.
Steve Kinney introduces the course by discussing the challenges of web security, as well as the importance of understanding the mental model of security on the web. This course will cover common vulnerabilities found in web applications and explore ways to break them open to gain a deeper understanding of web security. Steve walks through how to set up the course repository. He also explains the various options available, such as running the examples with npm start, enabling SQL query logging, choosing a different port, and cleaning the SQLite databases.
Steve walks through how to set up the course repository. He also explains the various options available, such as running the examples with npm start, enabling SQL query logging, choosing a different port, and cleaning the SQLite databases.
Cookies
Section Duration: 43 minutes
 Steve discusses how cookies are used to maintain a session and authenticate users, as well as how they can be used for tracking and advertising purposes. He also mentions the history and implementation of cookies and demonstrates how to view and delete cookies in the browser's developer tools.
Steve discusses how cookies are used to maintain a session and authenticate users, as well as how they can be used for tracking and advertising purposes. He also mentions the history and implementation of cookies and demonstrates how to view and delete cookies in the browser's developer tools. Steve discusses the attributes of a cookie, including expiration date and age. Steve also warns about using certain settings, such as the path and domain attributes, as they can have unintended consequences and potentially compromise security.
Steve discusses the attributes of a cookie, including expiration date and age. Steve also warns about using certain settings, such as the path and domain attributes, as they can have unintended consequences and potentially compromise security.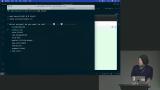 Steve discusses the importance of using libraries instead of writing your own code for tasks like parsing request bodies and handling security. He demonstrates how to use the Cookie Parser library to handle cookies in the app and points out the security issue of storing user information in plain text.
Steve discusses the importance of using libraries instead of writing your own code for tasks like parsing request bodies and handling security. He demonstrates how to use the Cookie Parser library to handle cookies in the app and points out the security issue of storing user information in plain text.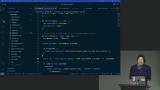 Steve explains how sessions provide a layer of abstraction between the user and their actual identity, allowing for more secure authentication and authorization processes. He also demonstrates how to set additional attributes on cookies, such as HttpOnly and secure.
Steve explains how sessions provide a layer of abstraction between the user and their actual identity, allowing for more secure authentication and authorization processes. He also demonstrates how to set additional attributes on cookies, such as HttpOnly and secure.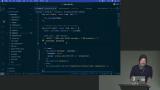 Steve demonstrates how to sign cookies using the cookie-parser plugin in Node.js and shows how signed cookies can prevent unauthorized tampering. He also introduces the concept of using sessions to abstract the user's identity and generate a unique session ID for each user.
Steve demonstrates how to sign cookies using the cookie-parser plugin in Node.js and shows how signed cookies can prevent unauthorized tampering. He also introduces the concept of using sessions to abstract the user's identity and generate a unique session ID for each user. Steve discusses the same origin policy, which is based on the tuple of protocol, host, and port, and if any of these elements are different, it is considered a different origin. He also briefly discusses the security vulnerabilities and protections associated with cookies.
Steve discusses the same origin policy, which is based on the tuple of protocol, host, and port, and if any of these elements are different, it is considered a different origin. He also briefly discusses the security vulnerabilities and protections associated with cookies.
Session Hijacking & Injection
Section Duration: 41 minutes
 Steve discusses more security exploits, including session hijacking, privilege escalation, and techniques such as investigating API responses, injecting CSS, and attempting man-in-the-middle attacks.
Steve discusses more security exploits, including session hijacking, privilege escalation, and techniques such as investigating API responses, injecting CSS, and attempting man-in-the-middle attacks.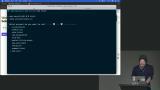 Steve demonstrates various security vulnerabilities in a web application. He show how an attacker can exploit SQL injection by manipulating input fields to bypass authentication and gain unauthorized access to user data. Steve also emphasizes the importance of logging and alerting to detect and respond to potential attacks.
Steve demonstrates various security vulnerabilities in a web application. He show how an attacker can exploit SQL injection by manipulating input fields to bypass authentication and gain unauthorized access to user data. Steve also emphasizes the importance of logging and alerting to detect and respond to potential attacks.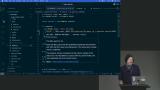 Steve discusses the benefits of using abstractions and ORM tools to minimize security vulnerabilities. He also mentions SQL injection and the potential harm it can cause, as well as the concept of stored queries as a security measure.
Steve discusses the benefits of using abstractions and ORM tools to minimize security vulnerabilities. He also mentions SQL injection and the potential harm it can cause, as well as the concept of stored queries as a security measure.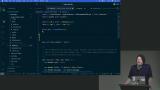 Steve discusses privilege escalation in applications that use NoSQL databases. He emphasizes the importance of implementing allow listing instead of deny listing to prevent such attacks. He also demonstrates how an attacker can manipulate request parameters using tools like cURL or the browser's network tab.
Steve discusses privilege escalation in applications that use NoSQL databases. He emphasizes the importance of implementing allow listing instead of deny listing to prevent such attacks. He also demonstrates how an attacker can manipulate request parameters using tools like cURL or the browser's network tab. Steve discusses man-in-the-middle attacks and the importance of using HTTPS in production environments. He covers various cookie attributes, such as HTTPOnly and SameSite, and explains the differences between site and origin. Steve also touches on injection attacks, including SQL injection and command injection, and briefly mentions file upload vulnerabilities and remote code execution as potential security risks.
Steve discusses man-in-the-middle attacks and the importance of using HTTPS in production environments. He covers various cookie attributes, such as HTTPOnly and SameSite, and explains the differences between site and origin. Steve also touches on injection attacks, including SQL injection and command injection, and briefly mentions file upload vulnerabilities and remote code execution as potential security risks.
Cross-Site Request Forgery
Section Duration: 59 minutes
 Steve discusses cross-site request forgery (CSRF) attacks, which involve tricking a user's browser into performing actions that they didn't intend to do without actually stealing their session token.
Steve discusses cross-site request forgery (CSRF) attacks, which involve tricking a user's browser into performing actions that they didn't intend to do without actually stealing their session token. Steve discusses how CSRF attacks can be executed by tricking a user's browser into making a malicious request without the need for injecting code. He also mentions the importance of protecting against CSRF attacks by implementing techniques such as secure cookie handling and unpredictable parameters.
Steve discusses how CSRF attacks can be executed by tricking a user's browser into making a malicious request without the need for injecting code. He also mentions the importance of protecting against CSRF attacks by implementing techniques such as secure cookie handling and unpredictable parameters.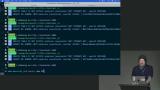 Steve demonstrates how a malicious user can exploit an application by sending a link that triggers a form submission and transfers money without the user's consent. He then explains different strategies for protecting against such attacks, including the use of same-site cookies and the distinction between sites and origins.
Steve demonstrates how a malicious user can exploit an application by sending a link that triggers a form submission and transfers money without the user's consent. He then explains different strategies for protecting against such attacks, including the use of same-site cookies and the distinction between sites and origins. Steve discusses the balance between user experience and security when setting cookie security levels.
Steve discusses the balance between user experience and security when setting cookie security levels.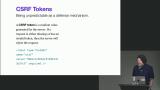 Steve demonstrates how to implement protection against CSRF attacks using tokens. He shows how to generate a unique token for each session, hide it in a form, and validate it on the server-side to prevent unauthorized requests.
Steve demonstrates how to implement protection against CSRF attacks using tokens. He shows how to generate a unique token for each session, hide it in a form, and validate it on the server-side to prevent unauthorized requests.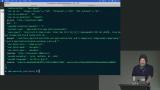 Steve instructs students to implement session management and CSRF protection in the provided social media application. He walks through the abstractions he created for creating and getting sessions, and how they set the cookie accordingly. He also shows how they handle the current user middleware and protect post requests with CSRF tokens.
Steve instructs students to implement session management and CSRF protection in the provided social media application. He walks through the abstractions he created for creating and getting sessions, and how they set the cookie accordingly. He also shows how they handle the current user middleware and protect post requests with CSRF tokens.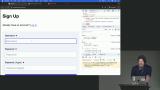 Steve demonstrates how a CSRF attack can occur by manipulating the app's code and sending unauthorized requests. He also discusses the risks of including personal information in query parameters and suggests alternative methods for CSRF protection, such as double-signing cookies or implementing multi-step actions.
Steve demonstrates how a CSRF attack can occur by manipulating the app's code and sending unauthorized requests. He also discusses the risks of including personal information in query parameters and suggests alternative methods for CSRF protection, such as double-signing cookies or implementing multi-step actions.
CORS & Cross-Site Scripting
Section Duration: 35 minutes
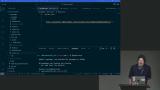 Steve discusses cross-origin resource sharing (CORS) and its role in allowing or restricting access to resources on different domains. He also covers the headers involved in CORS and provides insights on how to handle more nuanced security requirements using additional request security headers.
Steve discusses cross-origin resource sharing (CORS) and its role in allowing or restricting access to resources on different domains. He also covers the headers involved in CORS and provides insights on how to handle more nuanced security requirements using additional request security headers. Steve discusses cross-site scripting (XSS) attacks and provides examples of famous XSS attacks such as the Samy worm on Myspace and a Twitter worm. He explains how XSS attacks work, the different types of XSS attacks (stored, reflected, and DOM-based), and the techniques used to execute malicious code on a website.
Steve discusses cross-site scripting (XSS) attacks and provides examples of famous XSS attacks such as the Samy worm on Myspace and a Twitter worm. He explains how XSS attacks work, the different types of XSS attacks (stored, reflected, and DOM-based), and the techniques used to execute malicious code on a website. Steve discusses various real-life examples of security vulnerabilities and breaches that have occurred in the past. He mentions cases such as the TweetDeck worm, eBay's redirect vulnerability, Angular Sandbox flaw, British Airways data breach, Fortnite data access issue, and a vulnerability in a VS Code plugin.
Steve discusses various real-life examples of security vulnerabilities and breaches that have occurred in the past. He mentions cases such as the TweetDeck worm, eBay's redirect vulnerability, Angular Sandbox flaw, British Airways data breach, Fortnite data access issue, and a vulnerability in a VS Code plugin.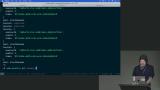 Steve discusses the importance of sanitizing inputs to prevent XSS attacks. He mentions that using a library like DOMPurify or utilizing built-in sanitization features in frameworks like React, Svelte, or Vue can help protect against XSS vulnerabilities. Steve also mentions the need for a second layer of defense, such as implementing a content security policy, to further protect against potential attacks.
Steve discusses the importance of sanitizing inputs to prevent XSS attacks. He mentions that using a library like DOMPurify or utilizing built-in sanitization features in frameworks like React, Svelte, or Vue can help protect against XSS vulnerabilities. Steve also mentions the need for a second layer of defense, such as implementing a content security policy, to further protect against potential attacks. Steve discusses the importance of input validation and sanitization in web development. He explain the concept of safe syncs and safe methods for sanitizing user input. He also mention the use of tools like DOM Purify and suggest running tests to ensure that the sanitization process is effective.
Steve discusses the importance of input validation and sanitization in web development. He explain the concept of safe syncs and safe methods for sanitizing user input. He also mention the use of tools like DOM Purify and suggest running tests to ensure that the sanitization process is effective.
Content Security Policy
Section Duration: 26 minutes
 Steve discusses utilizing a content security policy (CSP) as a second layer of defense against malicious code. He explains that CSP allows you to specify which domains are allowed to load resources, such as scripts and CSS, on your web page.
Steve discusses utilizing a content security policy (CSP) as a second layer of defense against malicious code. He explains that CSP allows you to specify which domains are allowed to load resources, such as scripts and CSS, on your web page.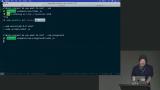 Steve demonstrates how to use CSP to prevent cross-site scripting attacks. He provides an example website with various vulnerabilities and then walks through the process of implementing CSP to mitigate those vulnerabilities. Steve explains the different directives and options available in CSP and emphasizes the importance of allowing only trusted sources and minimizing the attack surface.
Steve demonstrates how to use CSP to prevent cross-site scripting attacks. He provides an example website with various vulnerabilities and then walks through the process of implementing CSP to mitigate those vulnerabilities. Steve explains the different directives and options available in CSP and emphasizes the importance of allowing only trusted sources and minimizing the attack surface. Steve discusses two options for including inline scripts securely: using a nonce (number used once) or hashing the contents of the script. He explains how to implement each option and discusses the trade-offs between cache invalidation and security.
Steve discusses two options for including inline scripts securely: using a nonce (number used once) or hashing the contents of the script. He explains how to implement each option and discusses the trade-offs between cache invalidation and security.
Other Attack Vectors
Section Duration: 41 minutes
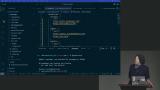 Steve discusses clickjacking, a type of attack that tricks users into performing malicious actions without their knowledge. He demonstrates an example of clickjacking and also explains some measures to protect against it, such as using frame options and content security policies.
Steve discusses clickjacking, a type of attack that tricks users into performing malicious actions without their knowledge. He demonstrates an example of clickjacking and also explains some measures to protect against it, such as using frame options and content security policies.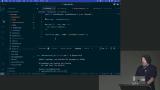 Steve discusses how an iframe can be injected with malicious code and how the code blindly accepts messages without checking their origin. He explains how to fix this vulnerability by whitelisting trusted domains and ensuring that messages are only accepted from those domains.
Steve discusses how an iframe can be injected with malicious code and how the code blindly accepts messages without checking their origin. He explains how to fix this vulnerability by whitelisting trusted domains and ensuring that messages are only accepted from those domains.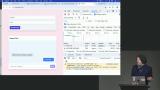 Steve discusses an attack called tabnabbing, which involves manipulating a user's browser tabs. He also mentions some measures to protect against this attack, such as using frame options, CSP headers, or breaking the connection between frames and windows.
Steve discusses an attack called tabnabbing, which involves manipulating a user's browser tabs. He also mentions some measures to protect against this attack, such as using frame options, CSP headers, or breaking the connection between frames and windows.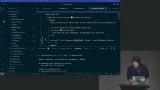 Steve discusses the concept of JSON Web Tokens (JWTs) as an alternative to traditional session management. He explains how JWTs work, including the encryption algorithm, data payload, and cryptographic hash. He also discusses the trade-offs and considerations when using JWTs, such as the lack of session storage and the need for trust in the token issuer.
Steve discusses the concept of JSON Web Tokens (JWTs) as an alternative to traditional session management. He explains how JWTs work, including the encryption algorithm, data payload, and cryptographic hash. He also discusses the trade-offs and considerations when using JWTs, such as the lack of session storage and the need for trust in the token issuer. Steve discusses different options for storing JWTs including local storage, session storage, and cookies. He also mentions the option of not storing JWTs and instead keeping them in memory, but note that this may be a feature or a bug depending on the use case. Steve provides code examples and emphasizes the importance of signing and verifying JWTs with the same secret and algorithm.
Steve discusses different options for storing JWTs including local storage, session storage, and cookies. He also mentions the option of not storing JWTs and instead keeping them in memory, but note that this may be a feature or a bug depending on the use case. Steve provides code examples and emphasizes the importance of signing and verifying JWTs with the same secret and algorithm.
Wrapping Up
Section Duration: 5 minutes
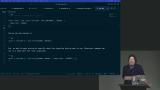 Steve wraps up the course by discussing the importance of encrypting passwords and introduces the concept of salting to add an additional layer of protection. He also mentions the use of secure key management services in cloud platforms to store and manage keys securely.
Steve wraps up the course by discussing the importance of encrypting passwords and introduces the concept of salting to add an additional layer of protection. He also mentions the use of secure key management services in cloud platforms to store and manage keys securely.
Learn Straight from the Experts Who Shape the Modern Web
- 250+In-depth Courses
- Industry Leading Experts
- 24Learning Paths
- Live Interactive Workshops

