Substack
Course Description
Dive into cryptography fundamentals and LevelDB to build stronger, more secure applications! Code with James Halliday as you pair modern cryptography and the modular NoSQL databases of LevelDB to help you fortify your communications systems.
This course and others like it are available as part of our Frontend Masters video subscription.
Preview
Course Details
Published: September 13, 2017
Rating
Learn Straight from the Experts Who Shape the Modern Web
Your Path to Senior Developer and Beyond
- 250+ In-depth courses
- 24 Learning Paths
- Industry Leading Experts
- Live Interactive Workshops
Table of Contents
LevelDB
Section Duration: 1 hour, 9 minutes
 James Halliday introduces and sets up LevelDB, a key-value storage library written at Google that provides an ordered mapping from string keys to string values.
James Halliday introduces and sets up LevelDB, a key-value storage library written at Google that provides an ordered mapping from string keys to string values. After James reviews the methods that are available with LevelDB, he notes that LevelDB uses lexicographic sorting, which alphabetical order of string values based on the alphabetical order. J
After James reviews the methods that are available with LevelDB, he notes that LevelDB uses lexicographic sorting, which alphabetical order of string values based on the alphabetical order. J With the LevelDB setup, James demonstrates how to organize keys for different situations such as a simple blog and creates queries against that data.
With the LevelDB setup, James demonstrates how to organize keys for different situations such as a simple blog and creates queries against that data. James introduces how to create multiple keys for each post to create a secondary index.
James introduces how to create multiple keys for each post to create a secondary index. With the database set up, James reviews how to build a system to add new data into LevelDB.
With the database set up, James reviews how to build a system to add new data into LevelDB. James adds new posts with timestamps to the database. Then James examines different ways to query that data from the LevelDB database.
James adds new posts with timestamps to the database. Then James examines different ways to query that data from the LevelDB database. James introduces Subleveldown, which a library for LevelDB that creates nested sub-databases with unique namespaces;
James introduces Subleveldown, which a library for LevelDB that creates nested sub-databases with unique namespaces; James installs Level-Livefeed package that allows for one to subscribe to a live feed of changes to the database.
James installs Level-Livefeed package that allows for one to subscribe to a live feed of changes to the database. To use LevelDB in the browser, James switches from level package to include level-browserify. This change allows the use of the LevelUP code to be portable making it work with node and in the browser.
To use LevelDB in the browser, James switches from level package to include level-browserify. This change allows the use of the LevelUP code to be portable making it work with node and in the browser. After reviewing the best use cases for LevelDB, James creates a demo application with LevelDB, node, and IndexedDB.
After reviewing the best use cases for LevelDB, James creates a demo application with LevelDB, node, and IndexedDB. James takes questions from the students about IndexedDB and LocalStorage, browser support, and more.
James takes questions from the students about IndexedDB and LocalStorage, browser support, and more.
Cryptography
Section Duration: 41 minutes
 James introduces hashes. While encryption is a two-step process used first to encrypt and then decrypt a message, hashing condenses a message into an irreversible fixed-length value or hash.
James introduces hashes. While encryption is a two-step process used first to encrypt and then decrypt a message, hashing condenses a message into an irreversible fixed-length value or hash.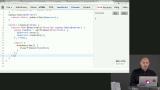 James discusses approaches to cryptography including random number generators, symmetric ciphers, and asymmetric crypto. Cipher is a shared algorithm for performing encryption or decryption whereas asymmetric crypto uses public and private keys to encrypt and decrypt data. James also notes that is an important tool with cryptography is picking a robust random number generator. Finally, James warns against creating your encryption process.
James discusses approaches to cryptography including random number generators, symmetric ciphers, and asymmetric crypto. Cipher is a shared algorithm for performing encryption or decryption whereas asymmetric crypto uses public and private keys to encrypt and decrypt data. James also notes that is an important tool with cryptography is picking a robust random number generator. Finally, James warns against creating your encryption process.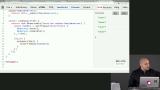 James introduces Sodium, a library for encryption, decryption, signatures, and password hashing. Then James demonstrates how to setup Chloride, which is based on Sodium, and generate key pairs.
James introduces Sodium, a library for encryption, decryption, signatures, and password hashing. Then James demonstrates how to setup Chloride, which is based on Sodium, and generate key pairs.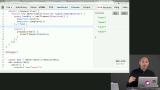 James discusses how to use Sodium cryptography with or without a signature, using a symmetric cipher, and using public key encryption.
James discusses how to use Sodium cryptography with or without a signature, using a symmetric cipher, and using public key encryption.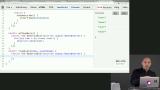 James reviews secret-handshake library, which is used to keep both parties unaware of each other with mutually authenticating key agreement handshake. James takes questions from students.
James reviews secret-handshake library, which is used to keep both parties unaware of each other with mutually authenticating key agreement handshake. James takes questions from students.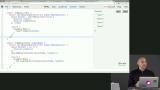 James reviews merkle DAGs, which is a directed acyclic graph whose objects are linked to each other (usually just by their hash), where the hash(object) includes all hash(linked_object).
James reviews merkle DAGs, which is a directed acyclic graph whose objects are linked to each other (usually just by their hash), where the hash(object) includes all hash(linked_object).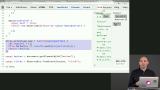 James demonstrates how to use merkle DAGs with node using shasum, which checks for SHA checksums.
James demonstrates how to use merkle DAGs with node using shasum, which checks for SHA checksums.
Kappa Architecture
Section Duration: 37 minutes
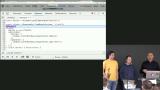 James introduces Kappa Architecture, where an immutable and append-only logs are used as the source of truth. To create these append-only logs, James notes that they are built hashes that are then trivial to replicate with concatenation.
James introduces Kappa Architecture, where an immutable and append-only logs are used as the source of truth. To create these append-only logs, James notes that they are built hashes that are then trivial to replicate with concatenation.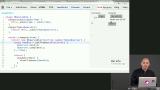 James reviews hyperlog, which creates append-only merkle DAG log store. Hyperlog also can link to other documents by cryptographic hash and provides hooks for cryptographic signing and verification. Then James shows how to set up hyperlog.
James reviews hyperlog, which creates append-only merkle DAG log store. Hyperlog also can link to other documents by cryptographic hash and provides hooks for cryptographic signing and verification. Then James shows how to set up hyperlog. James discusses how to synchronous two databases. James takes questions from students.
James discusses how to synchronous two databases. James takes questions from students.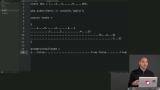 James reviews hyperlog-index, which builds materialized views on top of a hyperlog.
James reviews hyperlog-index, which builds materialized views on top of a hyperlog.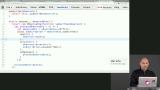 James shows hyperkv, which provides a p2p key/value store as a materialized view over a hyperlog. Then James discusses hyperlog-sodium, which more easily configures hyperlog for cryptographic signing.
James shows hyperkv, which provides a p2p key/value store as a materialized view over a hyperlog. Then James discusses hyperlog-sodium, which more easily configures hyperlog for cryptographic signing.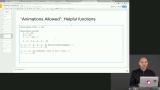 James reviews several examples of kappa architecture: P2P social database; map database built on hyperlog, hyperkv, hyperlog-kdb-index; and P2P file sync over an append-only merkle DAG log.
James reviews several examples of kappa architecture: P2P social database; map database built on hyperlog, hyperkv, hyperlog-kdb-index; and P2P file sync over an append-only merkle DAG log.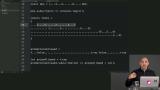 Create a swarm of P2P connections using WebRTC and a signalhub.
Create a swarm of P2P connections using WebRTC and a signalhub.
Learn Straight from the Experts Who Shape the Modern Web
- 250+In-depth Courses
- Industry Leading Experts
- 24Learning Paths
- Live Interactive Workshops

