Netflix
Course Description
Learn what it means to become a full-stack engineer. Get hands-on with setting up your own server to build and deploy web applications from scratch. You'll dive deep into servers, work with the command line, understand networking and security, set up continuous integration and deployment, manage databases, and build containers. Become a well-rounded engineer and gain the confidence that you can build any type of application!
This course and others like it are available as part of our Frontend Masters video subscription.
Preview
What They're Saying
nowdays there are a lot of tools to go/ship fast, but going back to basics was so refreshing, thanks jem

Luis Mauro Martinez Baez
Wow, I really enjoyed the ride! I've learned soo much. Really great course that gets you started on the full stack track.

Dennis Lemm
This course really covers usually ignored parts of the full-stack development path. 100% recommend it for software engineers.

Seruyange Joseph
Course Details
Published: April 18, 2023
Rating
Learning Paths
Learn Straight from the Experts Who Shape the Modern Web
Your Path to Senior Developer and Beyond
- 250+ In-depth courses
- 24 Learning Paths
- Industry Leading Experts
- Live Interactive Workshops
Table of Contents
Introduction
Section Duration: 21 minutes
 Jem introduces this course by sharing personal and professional background, course prerequisites, and social media handles. Modern computing, the concept of full stack engineering, and a brief overview of the course content are also discussed in this segment.
Jem introduces this course by sharing personal and professional background, course prerequisites, and social media handles. Modern computing, the concept of full stack engineering, and a brief overview of the course content are also discussed in this segment. Jem asks the workshop audience for their definitions of a full stack engineer and discusses what a tech stack is. Examples of some popular tech stacks and Jem's definition of a full stack engineer are also provided in this lesson.
Jem asks the workshop audience for their definitions of a full stack engineer and discusses what a tech stack is. Examples of some popular tech stacks and Jem's definition of a full stack engineer are also provided in this lesson.
Command Line
Section Duration: 30 minutes
 Jem discusses how the terminal and command line communicate with a computer, the benefits of using the command line, and demonstrates some common commands. Students are then instructed to in the command line create a "temp" directory that contains a "hello" file, list the directory contents, move out of the directory, and delete "temp".
Jem discusses how the terminal and command line communicate with a computer, the benefits of using the command line, and demonstrates some common commands. Students are then instructed to in the command line create a "temp" directory that contains a "hello" file, list the directory contents, move out of the directory, and delete "temp". Jem walks through the solution to the command line exercise and demonstrates using the manual.
Jem walks through the solution to the command line exercise and demonstrates using the manual.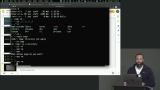 Jem provides some commands to use in case you get lost in the command line and how to switch modes in VIM. Students are then instructed to navigate to the home directory, create a "temp" directory, open a "test" file in VIM, write in the "test" file, and save and exit.
Jem provides some commands to use in case you get lost in the command line and how to switch modes in VIM. Students are then instructed to navigate to the home directory, create a "temp" directory, open a "test" file in VIM, write in the "test" file, and save and exit.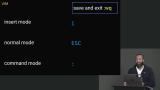 Jem walks through the solution to the VIM exercise and provides some resources for more information on VIM.
Jem walks through the solution to the VIM exercise and provides some resources for more information on VIM.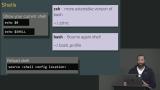 Jem discusses the application running in the terminal, the shell. Students are then instructed to open the shell config and add a line to make the shell tell you "good morning."
Jem discusses the application running in the terminal, the shell. Students are then instructed to open the shell config and add a line to make the shell tell you "good morning."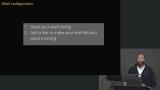 Jem walks through the solution to the shell exercise.
Jem walks through the solution to the shell exercise.
Server
Section Duration: 34 minutes
 Jem discusses a server as a computer that responds to a request and why servers are usually on dedicated hardware. The code to create a basic Node.js server is also provided in this segment.
Jem discusses a server as a computer that responds to a request and why servers are usually on dedicated hardware. The code to create a basic Node.js server is also provided in this segment.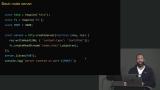 Jem walks through creating a simple server using Node.js and demonstrates some helpful tools, including nvm and homebrew. A brief discussion regarding ports, localhost, and reserved IP addresses is also covered in this segment.
Jem walks through creating a simple server using Node.js and demonstrates some helpful tools, including nvm and homebrew. A brief discussion regarding ports, localhost, and reserved IP addresses is also covered in this segment.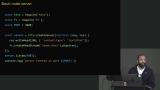 Jem discusses the limitations of local server hosting, server management, data centers, cloud computing, and virtualization. Most modern systems utilize cloud hosting providers instead of putting resources into managing servers in their own data centers.
Jem discusses the limitations of local server hosting, server management, data centers, cloud computing, and virtualization. Most modern systems utilize cloud hosting providers instead of putting resources into managing servers in their own data centers. Jem walks through how to buy and set up a VPS on Digital Ocean. This segment also covers how to choose a region and the importance of choosing an operating system with long-term support.
Jem walks through how to buy and set up a VPS on Digital Ocean. This segment also covers how to choose a region and the importance of choosing an operating system with long-term support.
Operating Systems
Section Duration: 55 minutes
 Jem discusses Windows and Unix-based operating systems and the multiple types of unix subsystems. The different layers of an operating system, including hardware, kernel, shell, and user, are also briefly discussed in this segment.
Jem discusses Windows and Unix-based operating systems and the multiple types of unix subsystems. The different layers of an operating system, including hardware, kernel, shell, and user, are also briefly discussed in this segment. Jem discusses server authentication, possible problems with usernames and passwords, and ssh keys. Dictionary attacks, MD5 hashing, the command line tool OpenSSL, and a brief discussion regarding Awk are also covered in this segment.
Jem discusses server authentication, possible problems with usernames and passwords, and ssh keys. Dictionary attacks, MD5 hashing, the command line tool OpenSSL, and a brief discussion regarding Awk are also covered in this segment.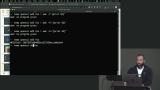 Jem demonstrates hashing with SHA256 and discusses increasing password security further by adding salt to introduce randomness into the hashing function. A student's question regarding the advantages of SHA1 over MD5, where the salt comes from, and what hash Bcrypt uses are also covered in this segment.
Jem demonstrates hashing with SHA256 and discusses increasing password security further by adding salt to introduce randomness into the hashing function. A student's question regarding the advantages of SHA1 over MD5, where the salt comes from, and what hash Bcrypt uses are also covered in this segment.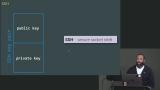 Jem discusses SSH keys which consist of a sharable public key and a private key, and walks through how to create an SSH key. Adding an SSH key to the Digital Ocean droplet and the commands needed to login to the server are also covered in this segment.
Jem discusses SSH keys which consist of a sharable public key and a private key, and walks through how to create an SSH key. Adding an SSH key to the Digital Ocean droplet and the commands needed to login to the server are also covered in this segment.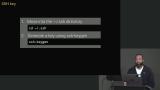 Jem quickly reviews creating an SSH key and logging into a server with that key. Modifying the SSH config to define the identity file automatically and adding the private key to keychain are also covered in this segment.
Jem quickly reviews creating an SSH key and logging into a server with that key. Modifying the SSH config to define the identity file automatically and adding the private key to keychain are also covered in this segment.
The Internet
Section Duration: 1 hour, 25 minutes
 Jem discusses the broad question of how the internet works and walks through a simplified diagram of how a computer can use the internet to connect to a server. Terminology, including internet, intranet, LAN, and WAN are also covered in this segment.
Jem discusses the broad question of how the internet works and walks through a simplified diagram of how a computer can use the internet to connect to a server. Terminology, including internet, intranet, LAN, and WAN are also covered in this segment. Students are instructed to check the status of a network host with ping, follow the path of a request using traceroute, and show the network status with netstat. A demonstration of each of these network tools is also provided in this segment.
Students are instructed to check the status of a network host with ping, follow the path of a request using traceroute, and show the network status with netstat. A demonstration of each of these network tools is also provided in this segment.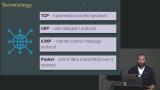 Jem discusses some of the terminologies used when referring to the internet and networking, including TCP, UDP, ICMP, and Packet. Examples of when UDP would be used instead of TCP are also discussed in this segment.
Jem discusses some of the terminologies used when referring to the internet and networking, including TCP, UDP, ICMP, and Packet. Examples of when UDP would be used instead of TCP are also discussed in this segment. Jem discusses the meaning and function of DNS, nameservers, and URL. An exercise in looking up domain names with nslookup and dig and a breakdown of the anatomy of a URL are also covered in this segment.
Jem discusses the meaning and function of DNS, nameservers, and URL. An exercise in looking up domain names with nslookup and dig and a breakdown of the anatomy of a URL are also covered in this segment. Jem discusses some restrictions when purchasing domain names, demonstrates how to purchase a domain name through Namecheap, and how to connect that domain to the previously created droplet on Digital Ocean.
Jem discusses some restrictions when purchasing domain names, demonstrates how to purchase a domain name through Namecheap, and how to connect that domain to the previously created droplet on Digital Ocean.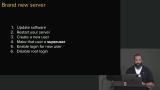 Jem walks through updating a new server's software and how to restart a server.
Jem walks through updating a new server's software and how to restart a server.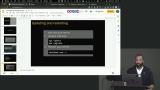 Jem discusses why running a server on the root is dangerous, and demonstrates how to create a new user, add a user to the "sudo" group, switch user, and check sudo access. Adding authorized ssh keys to the server is also covered in this segment.
Jem discusses why running a server on the root is dangerous, and demonstrates how to create a new user, add a user to the "sudo" group, switch user, and check sudo access. Adding authorized ssh keys to the server is also covered in this segment.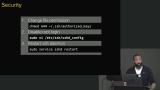 Jem walks through updating the file permission authorized keys and disabling logging into the root to prevent unauthorized access to the server.
Jem walks through updating the file permission authorized keys and disabling logging into the root to prevent unauthorized access to the server.
Application Setup
Section Duration: 35 minutes
 Jem walks through installing the Nginx web server and using it to route server requests. A brief discussion regarding installing the latest Node.js source is also covered in this segment.
Jem walks through installing the Nginx web server and using it to route server requests. A brief discussion regarding installing the latest Node.js source is also covered in this segment.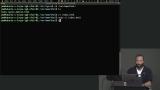 Jem walks through establishing the application file system and how to no longer require sudo by changing the application ownership and initializing a git repo.
Jem walks through establishing the application file system and how to no longer require sudo by changing the application ownership and initializing a git repo. Jem walks through setting up a virtual server block, answers a student's question regarding why nginx is being used and not Node.js, and installs the process manager PM2. PM2 will allow the server to continue running even if the terminal is closed and will restart the server if there is a server error.
Jem walks through setting up a virtual server block, answers a student's question regarding why nginx is being used and not Node.js, and installs the process manager PM2. PM2 will allow the server to continue running even if the terminal is closed and will restart the server if there is a server error.
Git
Section Duration: 16 minutes
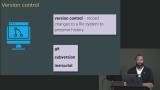 Students are instructed to create a git repository, create an SSH key called gh_key, add the SSH key to GitHub, add the remote repo, ensure the new SSH key is used, and push the local repo to Github.
Students are instructed to create a git repository, create an SSH key called gh_key, add the SSH key to GitHub, add the remote repo, ensure the new SSH key is used, and push the local repo to Github.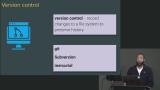 Jem discusses version control using git and walks through connecting to GitHub the Git exercise. Helpful commands in case you get stuck are also provided in this segment.
Jem discusses version control using git and walks through connecting to GitHub the Git exercise. Helpful commands in case you get stuck are also provided in this segment.
Security
Section Duration: 23 minutes
 Jem discusses potential security risks if someone gains unauthorized access to the server, including running through bandwidth caps, gaining access to GitHub and stealing information, and deleting auth log files to hide their tracks.
Jem discusses potential security risks if someone gains unauthorized access to the server, including running through bandwidth caps, gaining access to GitHub and stealing information, and deleting auth log files to hide their tracks. Jem discusses ports, how to view a list of well-known ports, and walks through installing and using nmap to view open ports.
Jem discusses ports, how to view a list of well-known ports, and walks through installing and using nmap to view open ports. Jem walks through managing port access with a firewall using the software ufw to allow access to ssh and http.
Jem walks through managing port access with a firewall using the software ufw to allow access to ssh and http. Jem discusses the meaning behind the numbers and various iterations of r, w, and x used when changing file permissions. A permissions cheat sheet is also provided in this segment.
Jem discusses the meaning behind the numbers and various iterations of r, w, and x used when changing file permissions. A permissions cheat sheet is also provided in this segment. Jem quickly demonstrates how to keep applications up to date automatically using unattended-upgrades.
Jem quickly demonstrates how to keep applications up to date automatically using unattended-upgrades.
Continuous Integration & Deployment
Section Duration: 50 minutes
 Jem discusses the need for continuous integration and continuous deployment when scaling applications. The differences between CI and CD, and the importance of testing are also covered in this segment.
Jem discusses the need for continuous integration and continuous deployment when scaling applications. The differences between CI and CD, and the importance of testing are also covered in this segment.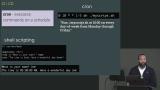 Jem discusses creating a CI/CD using a Unix stopwatch and cron to execute a shell script that pulls production updates on a set interval. A walkthrough of creating a simple bash script and cron job is also covered in this segment.
Jem discusses creating a CI/CD using a Unix stopwatch and cron to execute a shell script that pulls production updates on a set interval. A walkthrough of creating a simple bash script and cron job is also covered in this segment. Jem discusses logs and different options for how to read them, including tail, head, less, and cat. Standard streams and redirection commands are also covered in this segment.
Jem discusses logs and different options for how to read them, including tail, head, less, and cat. Standard streams and redirection commands are also covered in this segment. Jem demonstrates the syntax for searching for where a file name is and searching for file contents using the find and grep commands. A walk through of using both of these commands is also covered in this segment.
Jem demonstrates the syntax for searching for where a file name is and searching for file contents using the find and grep commands. A walk through of using both of these commands is also covered in this segment. Jem discusses redirection with Nginx, and compression with gzip, briefly demonstrates what compression is, and the difference between hashing and compression.
Jem discusses redirection with Nginx, and compression with gzip, briefly demonstrates what compression is, and the difference between hashing and compression. Jem walks through how to create a subdomain, including creating the corresponding A record, creating the server, and updating the nginx.conf file to recognize the new subdomain. Subdomains can be restricted from public access, making them useful for development sites.
Jem walks through how to create a subdomain, including creating the corresponding A record, creating the server, and updating the nginx.conf file to recognize the new subdomain. Subdomains can be restricted from public access, making them useful for development sites.
Realtime & Databases
Section Duration: 1 hour, 35 minutes
 Jem discusses real-time communication between the client and the server using websockets. Configuring nginx to allow connection to websockets and creating a new server with Express are also covered in this segment.
Jem discusses real-time communication between the client and the server using websockets. Configuring nginx to allow connection to websockets and creating a new server with Express are also covered in this segment. Jem briefly discusses possible errors when cloning the GitHub repository and demonstrates enabling websockets on the previously created server using Express. Writing a broadcast function, broadcasting the number of clients, and welcoming new client connections are also covered in this segment..
Jem briefly discusses possible errors when cloning the GitHub repository and demonstrates enabling websockets on the previously created server using Express. Writing a broadcast function, broadcasting the number of clients, and welcoming new client connections are also covered in this segment..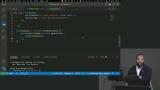 Jem demonstrates creating a websocket connection in the index.html, setting websocket protocols for both http and https, and setting where the websocket is connecting to. Updating the GitHub script to run npm install is also covered in this segment.
Jem demonstrates creating a websocket connection in the index.html, setting websocket protocols for both http and https, and setting where the websocket is connecting to. Updating the GitHub script to run npm install is also covered in this segment.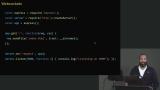 Jem discusses the benefits of using databases for data storage, including organization, scalability, and performance. An overview of relational compared to non-relational databases is also covered in this segment.
Jem discusses the benefits of using databases for data storage, including organization, scalability, and performance. An overview of relational compared to non-relational databases is also covered in this segment. Jem walks through using SQLite to create a database that contains a visitor log for the websocket server. Since this example uses memory, the database will reset whenever the server stops.
Jem walks through using SQLite to create a database that contains a visitor log for the websocket server. Since this example uses memory, the database will reset whenever the server stops. Jem discusses HTTP, what data is contained in headers, different meanings of status codes, and securing the connection with HTTPS.
Jem discusses HTTP, what data is contained in headers, different meanings of status codes, and securing the connection with HTTPS. Jem walks through installing and using certbot to secure the server connection and implement HTTPS. Opening the correct port with uncomplicated firewall is also covered in this segment.
Jem walks through installing and using certbot to secure the server connection and implement HTTPS. Opening the correct port with uncomplicated firewall is also covered in this segment. Jem discusses the different types of connections with HTTP/1.1 and HTTP/2. How to update the nginx server to HTTP2 is also covered in this segment.
Jem discusses the different types of connections with HTTP/1.1 and HTTP/2. How to update the nginx server to HTTP2 is also covered in this segment.
Containers
Section Duration: 36 minutes
 Jem discusses microservices and monolith software architectures, containers, how containers relate to cloud computing, and container management services.
Jem discusses microservices and monolith software architectures, containers, how containers relate to cloud computing, and container management services. Jem walks through how to create a docker container by installing docker using apt and creating a dockerfile.
Jem walks through how to create a docker container by installing docker using apt and creating a dockerfile. Jem discusses container orchestration and services used to manage containers, including Kubernetes and balancing request loads across multiple servers. A discussion regarding the different types of scheduling algorithms is also covered in this segment.
Jem discusses container orchestration and services used to manage containers, including Kubernetes and balancing request loads across multiple servers. A discussion regarding the different types of scheduling algorithms is also covered in this segment.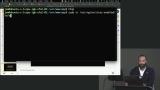 Jem walks through adding a load balancer to allow nginx to decide which server to pass the connection to.
Jem walks through adding a load balancer to allow nginx to decide which server to pass the connection to.
Wrapping Up
Section Duration: 6 minutes
 Jem wraps up the course by answering student questions, including what cores are, if it's valid to install nvm in the droplet, Netflix recommendations, security measures in the docker container, and if a container can be made locally and pulled in via GitHub. Recommendations for next steps and a brief overview of what was covered in the course are also provided in this lesson.
Jem wraps up the course by answering student questions, including what cores are, if it's valid to install nvm in the droplet, Netflix recommendations, security measures in the docker container, and if a container can be made locally and pulled in via GitHub. Recommendations for next steps and a brief overview of what was covered in the course are also provided in this lesson.
Learn Straight from the Experts Who Shape the Modern Web
- 250+In-depth Courses
- Industry Leading Experts
- 24Learning Paths
- Live Interactive Workshops




